
AMD Flaws Overview [Video]
Video uploaded by CTS Labs on March 13, 2018
Ryzen Falls: Thirteen Vulnerabilities Found in AMD Processors
True or False? That’s the question
We wrote before that AMD survived the Chip Apocalypse unscarthed. Today this giant also collapsed. The Israeli-based security company CTS-Labs found four classes of potential vulnerabilities in the Ryzen, EPYC, Ryzen Pro, and Ryzen Mobile processor line-ups which pretty sure rounds up all the chips the company is selling now. If we believe the whitepaper available for download on the site www.amdflaws.com nicknames the vulnerabilities as following: Masterkey, Ryzenfall, Fallout and Chimera.
Masterkey alledgedly affects primarily EPYC and Ryzen including EPYC Server, Ryzen Pro, Ryzen Mobile and simply Ryzen. It consists of three pathways to bypass Hardware Validated Boot on the Secure Processor itself. So, there are three vulnerabilities: Masterkey-1, Masterkey-2 and Masterkey-3. Once installed inside the Secure Processor, the malware is capable of running in kernel-mode with the top level permissions. In a nutshell, it can infect not only the operating system but also the BIOS, the Firmware Trusted Platform Module (fTPM) and the Secure Encrypted Virtualization (SEV).
Ryzenfall is dangerous for Ryzen, Ryzen Pro and Ryzen Mobile through the set of design and implementation flaws inside AMD Secure OS. The worst scenario that can take place is the main processor completely overtaken by a malware. Any such malware can easily leverage ARM Trust Zone® technology that normally secure isolation between system components. With this isolation compromised a hacker can get an access for secure storage of passwords and cryptographic keys. According to the number of flaws there are four iterations of the vulnerability: Ryzenfall-1, Ryzenfall-2, Ryzenfall-3 and Ryzenfall-4. Ryzenfall-1 embraces Ryzen, Ryzen Pro and Ryzen Mobile, but the other three spared the mobile version of the AMD CPU.
Fallout threatens the boot loader component of the EPYC’s Secure Processor. The boot loader is responsible for Hardware Validated Boot on EPYC servers and won’t affect the home computers much. But Fallout allows to get an access to the protected memory regions that normally are sealed off by the hardware. These regions usually contains sensible information like biometric ID data and personal credentials. The malware can disguise itself as the third-party signed driver. This class of vulnerabilities consists of Fallout-1, Fallout-2 and Fallout-3.
The most outrageous is the fourth class of vulnerabilities, that cannot be patched. They are hidden MANUFACTURER BACKDOORS inside AMD’s Promontory chipsets.
Chimera affects AMD’s Promontory chipset in both Ryzen and Ryzen Pro. The chipset links the CPU to external devices such as Hard Drives, USB devices, PCI Express cards, as well as network, Wi-Fi, and Bluetooth controllers. The malicious scenarios are numerous. From a hidden keylogger to unauthorized network access to say nothing about the memory protection bypass. In other words, your AMD-based PC doesn’t belong to you but to everyone else. The Taiwanese chip manufacturer ASMedia that made this chipsets has to answer some very unpleasant questions. Backdoors can be installed deliberately, they cannot be attributed to some production line malfunctions.
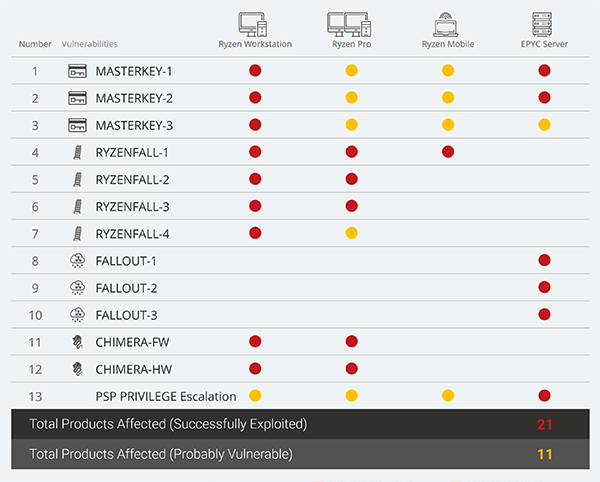
AMD Vulnerabilities Map
Perhaps, the manufactured backdoors in the most popular CPUs is the reason why CTS-Labs didn’t inform the AMD company in secret but went public. The AMD on the other hand expressed a serious doubt that a previously unknown security company had run into such serious vulnerabilities:
“We have just received a report from a company called CTS Labs claiming there are potential security vulnerabilities related to certain of our processors. We are actively investigating and analyzing its findings. This company was previously unknown to AMD and we find it unusual for a security firm to publish its research to the press without providing a reasonable amount of time for the company to investigate and address its findings. At AMD, security is a top priority and we are continually working to ensure the safety of our users as potential new risks arise. We will update this blog as news develops.”
Surprisingly the CTS Labs whitepaper follows in the wake of the U.S security agencies’ report in February. The report warns the U.S government that the Chinese manufactured chips can contain backdoors for collecting sensitive and secret data. The timing can be just a coincidence, though.
Anyway, we should wait till the AMD rolls out some plausible explanation to all that and keep the fingers crossed.
Surprisingly the CTS Labs whitepaper follows in the wake of the U.S security agencies’ report in February. The report warns the U.S government that the Chinese manufactured chips can contain backdoors for collecting sensitive and secret data. The timing can be just a coincidence, though.
On the other hand, the CTS Labs appeared out of nowhere, lacking any history or background. The site that posted the list of exploits has no safe https connection in the address. This is more than strange for the cyber-security company. The aggressive press release was prepared by Bevel PR but when the team of gamenexus.net tried to reach out the contact, they went to a full inbox. Further research revealed that Bevel PR has but one and the only employee Jessica Schaefer.
Well, lots of start-ups are understaffed at the beginning. But at the closer look the CTS Labs falls apart as the house of cards. The YouTube channel is a few days old, the offices in the videos are make-beliefs from a footage stock. It seems, the CTS Labs started up to announce about the AMD flaws and sink into the oblivion.
We don’t say that AMD chips are flawless. The chip-making industry has come to the point where the CPUs layouts and firmware should be thoroughly revisioned. The Meltdown and Spectre incident set a protocol to manage the matter. Any cyber-security lab or foundation should have immediately but secretly inform the chip-maker for double check and further research.
The whole event with the AMD vulnerabilities can be a frame up to drop the value of the AMD stock since the fist media to post the news was Viceroy Research. This anonymous research group focuses on “entities that … have signs of accounting irregularities and potential fraud”. Exactly what can be defined as such in the AMD activity we don’t know.
Anyway, whoever was behind this scheme, they made the best of the public fear of the hardware flaws.
Update!:
Linus Torvalds, the creator of the Linux OS, cracked down on the CTS Labs for lack of ethics. In the discussion on Google+ Mr. Torvalds said that bogus security companies can ruin the public’s trust. “People will start to ignore security and think “oh well, everything seems to be equally insecure these days (ARM, Intel, AMD) so what the point worrying about it?”, he wrote. He also added that credible researchers will have hard times being mixed up with the attention whoring companies.
Links
- AMD security flaw found in Ryzen, EPYC chips – CNET.
- Thinking to sell your old phone, tablet or computer? iGotOffer is the best place to sell smartphones and other devices online.
- Everything About Apple’s Products – The complete guide to all Apple consumer electronic products, including technical specifications, identifiers and other valuable information.
- Everything About Microsoft’s Products – The complete guide to all Microsoft consumer electronic products, including technical specifications, identifiers and other valuable information.





Facebook
Twitter
RSS