
CCleaner Infected With Malware: Update Now! — Equifax Updates — BlueBorne Hits Bluetooth – Threat Wire [Video]
Video uploaded by Hak5 on September 19, 2017
BlueBorne: Bluetooth Soft Spot
How many Bluetooth devices do you have? How many of them are paired with your smartphone or desktop right now? I, personally, have one – a fitness tracker tethered to my Android smartphone. I have it turned on 24/7 because I take my physical health very seriously and am interested in tracking it. I am sure you have some sort of tracker or some other device that is running on bluetooth as well. I’m sure you too have a tracker, or a keyboard, or a headphone set. The headphone cords can be so annoying!
There was something I read a few days ago that has me rethinking about keeping any devices connected to bluetooth on. I read something about called Blueborne, and now I think I may prefer to use my good ole’ wired headphones instead while outdoors. There has been a bunch of Bluetooth vulnerability discovered and you may start to feel the same as me after you read this blog.
Professionals from The Armis Labs discovered this “Blueborne” just a few weeks ago. The bad news is that this affects all kinds of Bluetooth devices. It also embraces all platforms: iOS, Android, Windows, even Linux! The worst part is that no antivirus can even block the attack!
Of course, all air connections are vulnerable, Wi-Fi included. They are radio waves after all, and people have been able to intercept radio waves for more than 80 years already. But Bluetooth is too much of a complicated system…and complexity doesn’t always mean integrity.
Hackers use any holes they can find in Bluetooth layouts to gain the control over your device from the start. Yes, your Bluetooth connection is the fastest way to get to your system.
This is the reason why no antivirus can help prevent any of this from even happening. An antivirus deals with codes – the malicious software that is written in a coded language. But the Bluetooth attack is executed by technical equipment in the physical world and therefore an antivirus does not detect it.
The latest research reports show that there are 8 billion connected or IoT devices in the world today. One billion are Apple, two billion are Android, and another two billion are Windows devices. The last three billion are random devices that are connected to Bluetooth, like smart boxes, smart bulbs, smart teapots, and etc. All of these devices share the same Bluetooth protocol. This explains why spreading malware via Bluetooth is one of the easiest things to do.
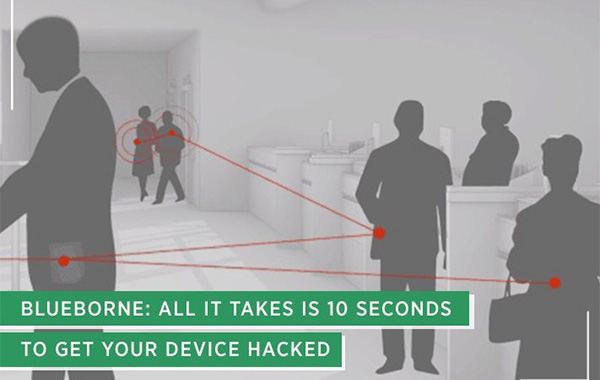
BlueBorne: All it Takes is 10 Seconds to Get Your Device Hacked. Image source: PakWired.com.
There are eight different kinds of vulnerabilities, four of them being critical to our security. They allow hackers to take complete control over your device. Unfortunately even putting your phone in undiscoverable mode won’t help. Cyber criminals don’t even have to pair their devices with yours. These viruses are spread by air, and can easily spread from one device to another. This is very similar to the flu virus that humans catch and easily spread.
Humans have the advantage of getting a vaccine or putting on a mask in public places when catching the flu. With a Bluetooth attack it’s enough to just have the connection toggle be swiped in the ‘on’ position. Bluetooth enabled devices are designed to constantly search for incoming connections from any devices, even when they are already paired.
This means your smartphone, desktop, or laptop is constantly searching the air for any Bluetooth signal at all. If it finds a signal, it connects and you won’t even be aware of it. You won’t get any notification that your laptop is pairing to a strange device. There are no dialogue boxes, no tray icons, nothing whatsoever notifying you about this. This makes the BlueBorne attack the most dangerous security threats of all.
List of impacted devices, threats and their solutions
Android
Devices impacted: all Android phones, tablets, and wearables excluding those using only the Bluetooth Low Energy (Google Pixel, Samsung Galaxy, Samsung Galaxy Tab, LG Watch Sport, Pumpkin Car Audio System).
Vulnerabilities: remote code execution, information leak and a Man-in-The-Middle attack.
Scanning software: Armis BlueBorne Scanner App on Google Play.
Solution: an update patch from August 7th, 2017 for Google; an update patch from September 9, 2017 for Google’s partners.
Windows
Devices impacted: all Windows computers since Windows Vista.
Vulnerabilities: a Man-in-The-Middle attack (aka “Blue Pineapple”).
Solution: security patches to all supported Windows versions on July 11, 2017, with a coordinated notification on Tuesday, September 12.
Linux
Devices impacted: Samsung Gear S3 (Smartwatch), Samsung Smart TVs, Samsung Family Hub (Smart refrigerator).
Vulnerabilities: leak vulnerability (Linux BlueZ), remote code execution (Linux from version 3.3-rc1).
Solution: Leak vulnerability. Remote code execution.
iOS
Devices impacted: All iPhone, iPad and iPod touch devices with iOS 10 and lower, AppleTV devices with version 7.2.2 and lower.
Vulnerabilities: remote code execution vulnerability.
Solution: latest iOS or tvOS available.
Links
- Are you switching to a new device? Sell your old one online for top dollar. The best place to sell your used gadgets online: iGotOffer.com
- Everything About Apple’s Products – The complete guide to all Apple consumer electronic products, including technical specifications, identifiers and other valuable information.






Facebook
Twitter
RSS