
CISA director: The LOG4J security flaw is the ‘most serious’ she’s seen in her career [Video]
Video uploaded by CNBC Television on December 20, 2021
The potential ultimate backdoor in your devices: keep your eyes open for the Log4J vulnerability
Yes, it’s the same old – and seemingly never-ending – story again: our gadgets are under yet another threat again, and this one seems to be an extreme one indeed, even taking into account the inescapable hype element involved in any news of this sort.
After all, it’s not often that all the cybersecurity experts of every notable player, British and American alike, from Checkpoint and Sophos to UK’s National Cyber Security Centre and Microsoft (and without a single jab at the latter, mind), in unanimous agreement, stress the seriousness of the danger and intensity of the assaults by hackers trying to exploit the weakness in question (and 100+ attacks per minute is a truly scary piece of statistics, if you ask us). It looks like the “opening” created when the Javascript loads the Apache Log4J error messages library exceedingly appeals to all sorts of the Internet predators… and for a good (or rather bad) reason.
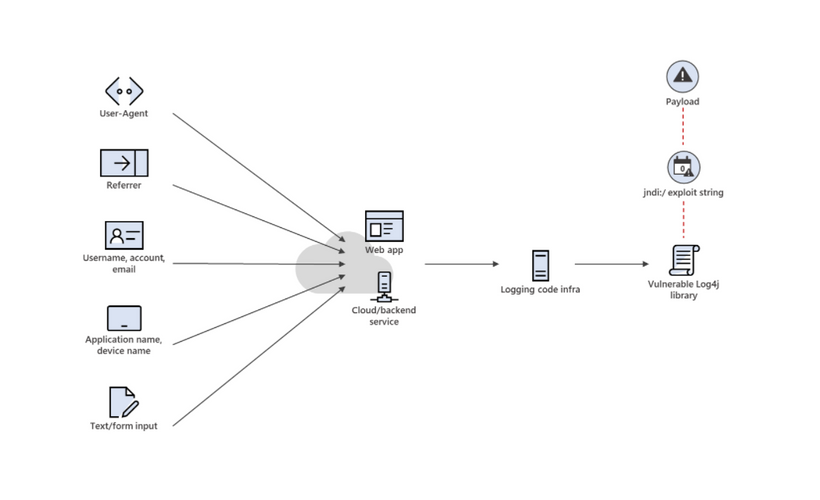
It looks like the “opening” created when the Javascript loads the Apache Log4J error messages library exceedingly appeals to all sorts of the Internet predators… and for a good (or rather bad) reason.
Because it appears to all but invite the unbidden guests to your data kept in any online applications you work with, as long as it has anything to do with the above library. And it is used by a lot of them, from cloud storage to email. Simply (and shortly) put, this particular flaw (which is also called “Log4Shell”) can remove even the already-not-impenetrable login/password barrier between the Web user and the Net fraudsters. There is no need for them to guess, deduce or buy your access information, because the subject flaw can allow them to get in anonymously. That’s something of a first, we must agree: the system itself, instead of just giving you not too adequate protection (to which most of us are used by now), actually works for the opposing team, so to speak. No wonder the said team is so eager to utilize this unexpected gift, first discovered this month: with it, they may get pretty much everything from unsuspecting users, from bank data to their very identities… and give them a lot of unwanted stuff instead. Can you say “malware galore”? And your computer becoming someone else’s crypto mining station is one of the less terrifying prospects of those beginning to emerge under the present circumstances. (Even though this is the most popular goal of the exploiters so far, according to the latest news on the matter).
Plus (as if all of the above were not enough), many of the service providers – the actual companies managing the storages and applications under attack – are not even aware of the problem at the moment. And there are virtually all the big guns among those being, well, gunned for: Amazon, CCisco, JetBrains and Oracles are just a few of this long list.

And no, there is no gadget type that is safe from this particular threat.
And no, there is no gadget type that is safe from this particular threat, no matter how new and well-equipped: as long as it is online (which means pretty much “every single device” these days) and uses Apache Software Foundation’s products, it is potentially welcoming the intruders to your private details.
So what can you personally do about it, if even the large corporations and top experts (such as cyber-intelligence head at CheckPoint Lotem Finkelstein) sound rather fazed and perplexed at the time? Well, actually, not as little as you might think. As it often happens, the grassroot initiative is proving more effective – at least at present – than any large-scale strategy (if only because there is not much of that in sight so far: there are some urgently-issued protection software from Oracle, but mostly we just hear the announcements of firms “working on the problem”).
And your first course of action should be upgrading your threatened (that is, Apache-running) notebooks, phones and tablets to the 2.15.0 – or higher – version of the Log4J. Identify the offending software on every gizmo you have – which has now been made easier to do by the Netherland’s Cyber Security Center, where the list of such programs are stored – and go for it. If, however, something will prevent the update, you still can set the “log4j2.formatMSGNoLookups” value to “true”.

And your first course of action should be upgrading your threatened (that is, Apache-running) notebooks, phones and tablets to the 2.15.0 – or higher – version of the Log4J.
Then you have to make sure that the aforesaid alerts get through to the SOC (security operations center). And to strengthen your defenses, the CISA (Cybersecurity and Infrastructure Security Agency) suggests that you’ll also go for a web application firewall (WAF), with a special instruction to concentrate on, you guessed it, Log4J. (Though if you’ll go for the AWS’ WAF, this might not be necessary, for this company has already included this instruction in its latest version of the firewall, and the same goes for their CloudFront, ALB, AppSync and API Gateway).
Not that even all of the above will remove the threat completely, of course (and you’ll still have to activate attacks and access attempts alert on all of the aforementioned devices), but it will complicate the matters for the bot makers and senders hunting for your info and access to your gadgets considerably, and make them more vulnerable to discovery as well. And, if anything, this is a step in the right – and safe – direction.
Links
- Dangerous “Log4j” security vulnerability affects everything from Apple to Minecraft – XDA Developers
- Sell your pre-owned device online – iGotOffer






Facebook
Twitter
RSS