Behind the booming ransomware industry: How hackers hold businesses hostage [Video]
Video uploaded by DW News on September 4, 2021
Ransomware Named Royal is Wreaking Havoc Targeting Corporations
A ransomware operation named Royal is wreaking havoc, primarily targeting corporations with ransom demands ranging from $250,000 to over $2 million. The malware is being used by many hacker groups across the UK to successfully penetrate networks using Google ads and search results. The hackers use “free” software download site which oftentimes look very legitimate to trick users into downloading the malware.
They also use contact forms on business websites, emails, fake forum comments, and blog posts. This malware is relatively new, first flagged at the start of 2022 and it is used to gain access to a victim’s environment, encrypt their data, and extort a ransom to return access to any files touched. The hacker group often uses callback phishing attacks where they impersonate food delivery or software providers in emails pretending to be subscription renewals. They often include a contact number in these phishing emails victim can contact to cancel the subscription service. When a victim calls the number, the group uses “social engineering” to convince the victim to install remote access software, which is used to gain initial access to the network. Once they gain access, they use Cobalt Strike, steal credentials, and spread through the Windows domain, steal data, and ultimately encrypt devices.
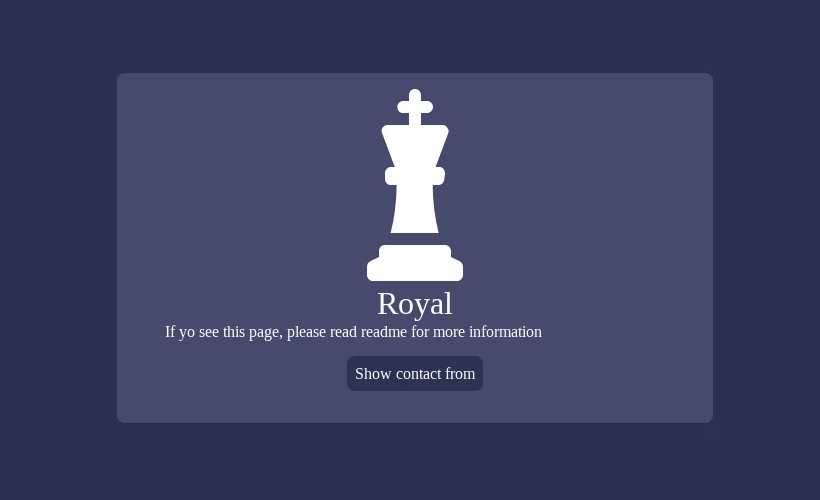
This “Royal” ransomware encrypts files and changes all the files extensions to “.royal” and an updated version of the same malware changes file extensions to “.royal_w” extension. It also creates a text file (named “README.TXT”) containing a ransom note.
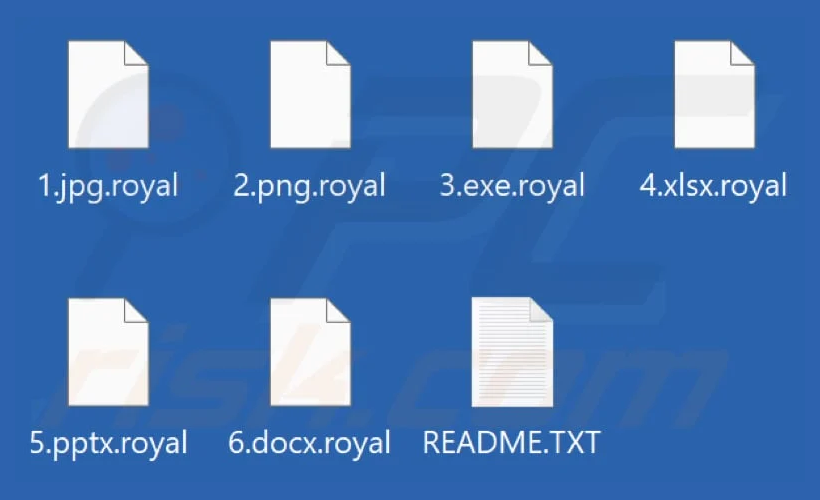
This “Royal” ransomware encrypts files and changes all the files extensions to “.royal” and an updated version of the same malware changes file extensions to “.royal_w” extension. It also creates a text file (named “README.TXT”) containing a ransom note. This is similar to BlackCat and ZEON ransomwares that generate similar ransom notes in their attacks. An example of how Royal ransomware renames files: it changes “1.jpg” to “1.jpg.royal”, “2.png” to “2.png.royal”, “3.exe” to “3.exe.royal”. The ransom note states that victims cannot access their files because they are encrypted and goes on to threaten that all files may be published online and become accessible to other cybercriminals, government institutions, and everyone else. In the ransom note, the group threatens not only to release data captured from the victim, but also putting a victim’s data out of reach via encryption unless the ransom demand is met which is “double extortion.” The group also suggests that this ordeal is simply a “pentesting service” and in what appears to be tongue-in-cheek offers to provide the victim with a “security review.” The ransom note also contains a link to the victim’s private Tor negotiation page.
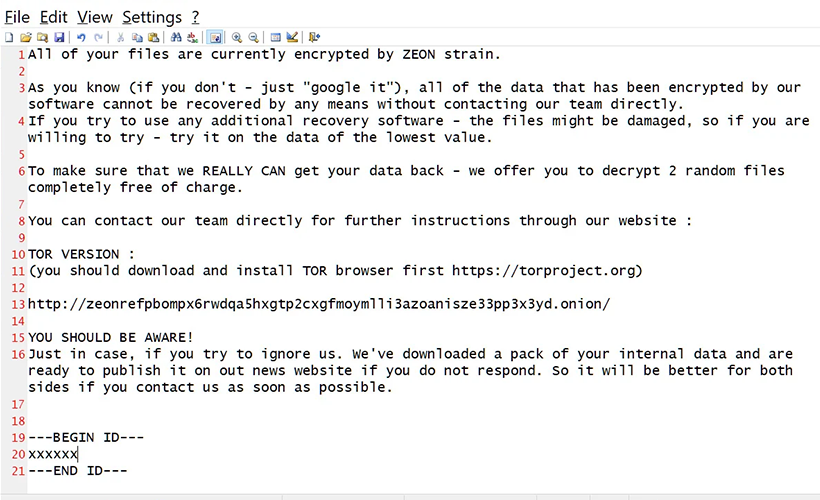
A Tor negotiation site is just a chat screen where the victim can communicate with the Royal ransomware attackers. The attackers are known to demand a ransom between $250,000 and over $2 million.
A Tor negotiation site is just a chat screen where the victim can communicate with the Royal ransomware attackers. The attackers are known to demand a ransom between $250,000 and over $2 million. They may also decrypt a few files for the victims to prove their decryptor works and share file lists of the stolen data. Research into this ransomware has shown that the ransomware is a 64-bit Windows executable written in C++, launched via command line which would suggest that it is programmed to be run via an operator after access to network through another method. The attackers make users to download the embedded in the BATLOADER and once launched it uses MSI Custom Actions to launch malicious PowerShell activity or run batch scripts to aid in disabling security solutions and lead to the delivery of various encrypted malware payloads that are decrypted and launched with PowerShell commands. In addition to this, the hackers also use NSudo to launch programs with special privileges and bypass security by adding registry values that are designed to disable antivirus softwares in the victim’s computer. Microsoft is tracking this malware codenamed DEV-0569 and say that the ransomware activity is on the rise and many corporations have fallen victim to this type of attack. Microsoft suggests users to use updated network protection and Microsoft Defender SmartScreen to help thwart malicious link access. Microsoft Defender for Office 365 can help flagging phishing emails and URL for known patterns.
Since DEV-0569’s phishing scheme abuses legitimate services, organizations can also leverage mail flow rules to capture suspicious keywords or review broad exceptions, such as those related to IP ranges and domain-level allow lists. Enabling Safe Links for emails, Microsoft Teams, and Office Apps can also help address this threat. Avoiding the use of domain-wide, admin-level service accounts and restricting local administrative privileges can also curb the attacks by avoiding installation of unwanted applications. The company also suggests users to enable cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus as this enable the AI to quickly identify and stop new and unknown threats.
Links
- New Royal Ransomware emerges in multi-million dollar attacks – BleepingComputer
- Sell your pre-owned device online – iGotOffer






Facebook
Twitter
RSS