
Understanding STIR/SHAKEN [Video]
Video uploaded by Bandwidth on December 1, 2020
We’re Still Fighting: What to Put Against the Nuisance Calls
OK, we admit it (yes, we can do that). We were wrong. Happens to the best of us, mind, but we were. At least, it was an honest mistaken belief. We sincerely thought that we were surely – if slowly – approaching the point of generally beating those pesky nuisance calls that clogged our lines, wasted our time and more often than not posed an actual danger to our privacy and our wallet (which they still do). We did expect that all this was relatively close to becoming our collective past thanks to the Stir/Shaken technique the FCC had recently made compulsory to the providers.
Well, it is not. The nuisance calls are still very much with us for the time being, and, quite likely, for the foreseeable future.
Mind you, it doesn’t mean that the Stir/Shaken method – which comes down to tracking the source of all the calls on all the wireless networks – has no use or brought no improvement whatsoever. According to both the latest figures and the public feedback, the overall amount of the unsolicited calls dropped noticeably, which is always a good thing. So it’s an effective approach, just not as effective as one could previously think. (One reason for this is that some of those calls are actually genuine in a way, but still unwanted or even unsafe, like those endless ads or uncalled-for warnings). So, maybe next time and all that.
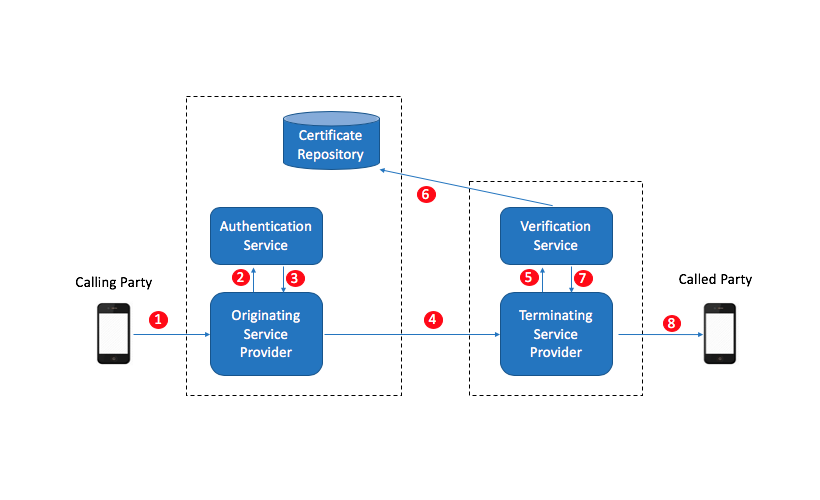
Stir/Shaken call flow.
However, what it certainly isn’t to say, is that we have to lie back and enjoy it here and now. Where the government’s law and big technologies can’t quite make it, some grassroot-level tricks and tips can always come to the rescue. And we are certainly going to make up for the previous error of our ways by familiarising you with some of those useful practices to help you reduce the cold-calls bombardment even further.
Now, the most obvious – yet often neglected or forgotten – way to protect yourself is ignoring the calls coming from the numbers you have blocked previously (yes, quite a few of us do respond to those, too) or those your screen doesn’t show, or those looking unfamiliar. But the latter might be a problem, for we often can’t remember – or even know – every number that might be relevant for us at any given time. So, if you suspect this call coming from “I don’t quite remember this number” may be an important one, be alert to what you hear when you take it, because there are quite a few surefire giveaways, and all of them mean that it’s time to end the conversation. And the most clear-cut of them is when the caller’s first words are the question whether you hear them. Same goes for those who’ll ask you to press the number to be redirected somewhere: the only case when a legitimate company does it is when you call it yourself. It is also a good idea not to go on when a caller claims to represent any company, no matter how well-recognized. In fact, the bigger the alleged firm, the better it would be for you to disconnect and call this firm yourself to make sure that nobody tried to fool you. The fraudsters know the value of the brand reputation only too well.
Plus, it might sound like a child game rule, but seriously, never answer “Yes” to any unrecognized caller. Current technologies allow even a moderately skilled swindler to use your spoken consent for a whole array of sinister purposes, so if there is no other way to answer, just break the conversation: it’s seriously not worth it.

If you suspect this call coming from “I don’t quite remember this number” may be an important one, be alert to what you hear when you take it, because there are quite a few surefire giveaways, and all of them mean that it’s time to end the conversation.
Another important thing is not to let your guard down if a call seems to be local: there are ways to mislead you into thinking so when it really isn’t. So, again, it’s always preferable to check.
And finally: large-scale as the aforementioned call-tracing tech is, it is far from being alone in the field. The smaller, less sweeping software can also considerably increase your defenses against the spam calls. There are some OS-inbuilt options, such as recently-improved Call Screen by Google, which now can identify such calls and intercept them in time; Apple, too, can shut them up with the aptly-named “Silence Unknown Callers” phone feature. The carriers, not to be outdone by the gadget makers, also offer the screening / shielding / filtering applications to weed out the troublesome phone swindlers (Call Protect by AT&T and Scam Shield by T-Mobile are just a few of those). And then, there are both free and paid apps by other various makers, created for exactly that goal, which may replace or complement the ones you have but for some reason are not satisfied with. Hiya is one field-proven no charge filter, and to Apple phone owners willing to part with some cash for more safety, we’d recommend The Firewall. Don’t be discouraged by this generic name; this blocking service is well worth its $4 a month fee. Or you can go for tricking the tricksters and get your own “number of convenience” from Google: this Google Voice number will successfully mask your real number at the time of call, and it won’t cost you a cent.
So there you are. The time when the nuisance calls will become a thing of the past may not be upon us yet, but we certainly are not deprived of ways to get by in the meantime.
Links
- What You Need to Know About STIR/SHAKEN – TelNet Worldwide
- Sell your pre-owned smartphone online – iGotOffer






Facebook
Twitter
RSS