Apps: Security
- May 16, 2017Captain Jack Sparrow Kidnapped by Hackers!
Pirates of the Caribbean: Dead Men Tell No Tales – Official Trailer Video uploaded by Walt...
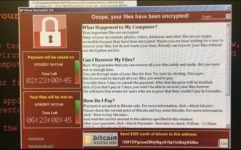
- May 13, 2017How to Protect Data from WannaCrypt
How to Protect Your Data from WannaCrypt Don’t WannaCry(pt) over lost files? Follow our Guide! 1 – Always...
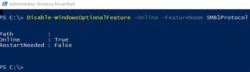
- May 13, 2017WannaCrypt Virus Stopped
WannaCrypt Virus Epidemic Stopped by Abracadabra The security expert @MalwareTechBlog stopped the WannaCrypt virus epidemy simply by...
- May 12, 2017Cyber Attack on NHS Hospitals in UK
Large-scale Cyber Attack on NHS Hospitals in UK USA Hospitals Are Intact So Far Today, May 12,...
- May 8, 2017Cats, Squirrels and Internet
Cats, Squirrels and Internet Have you got a cat? If you do, then you’re acquainted with your...
- May 6, 2017How Ultrasonic Sound Tracks Activity
How Ultrasonic Sound Tracks Your Activity Online I ever decide to start my own club, it will...
- May 5, 2017We Survived DDoS Attack
We Experienced a DDoS Attack but We’re Still Here Soon after postштп the article of the hacking...
- May 2, 2017The End of Innocence
The End of Innocence And Tips to Keep your Apple devices safe. For years, Windows users were...
- April 29, 2017VPN – Key to Security On-Line
VPN – Your Key to Security On-Line. Run Silent, Run Deep VPN are the three magic letters...
- April 22, 2017Net Neutrality Era Over?
Net Neutrality Era Over? We bet you’ve never heard of net neutrality, though you use the benefits...
- April 20, 2017BirckerBot: How Does Toaster Threaten National Security
BrickerBot: How Your Toaster Can Threaten National Security Sounds a bit loony, doesn’t it? How can a...
- March 22, 2017Electronic Gadgets Banned
Electronic Gadgets Banned on International Flights The UK has banned electronic gadgets on international flights from seven...
- February 7, 201776 iOS Apps VS. Your Privacy
76 iOS Apps Can Violate Your Privacy Says Sudo Security Sudo Security is the mobile security platform,...
- June 9, 2016When Bad Things Happen Online
When Bad Things Happen Online Anyone can receive unwanted sexual advances. The situation as it was seen...
- May 30, 2016Internet Safety Tips for Children and Teens
Many resources exist for kids on the Internet. However when the Internet was just beginning to take...
- May 27, 2016How to Childproof Computer
How to Childproof Computer It’s easier than you think to keep kids away from your files You...
- April 2, 2016How to Remove Petya Ransomware and Recover Data
How to Remove Petya Ransomware and Recover Data Petya is a new and powerful ransomware that targets...
- March 30, 2016Antivirus Software: It Does the Dirty Work
Do you remember the first antivirus programs? The following article goes back in time to shed light...
- June 12, 2015Secure Accounts, How to Secure PC Accounts
Secure Accounts: Ten Simple Steps to Secure PC and Online Accounts Secure Accounts: A secure password: Pick...
- February 26, 2015Smart Mobile Security Tips for Safe Online Browsing
Smart Mobile Security Tips for Safe Online Browsing Surfing the Internet, while certainly an enjoyable and pleasant...
Tap



















Facebook
Twitter
RSS